create app password office 365 powershell
Select the Create button and give the app password a name to indicate its purpose. Use the Microsoft Azure Active Directory Module for Windows PowerShell.
How To Connect Powershell To Office 365
Does anyone know of a way to manageremove app passwords using Powershell.

. The solve this problem you can create an App Password in Office 365. In this article you will learn how it works and how to set up things. App passwords are auto-generated and should be created and entered once per app.
The syntax for this looks an awfully lot like the New-User cmdlet in the standard Active Directory module. You can manage multiple domains simultaneously or script the commands to include a CSV file of as. In addition for the end-user manage app passwords you could refer to here.
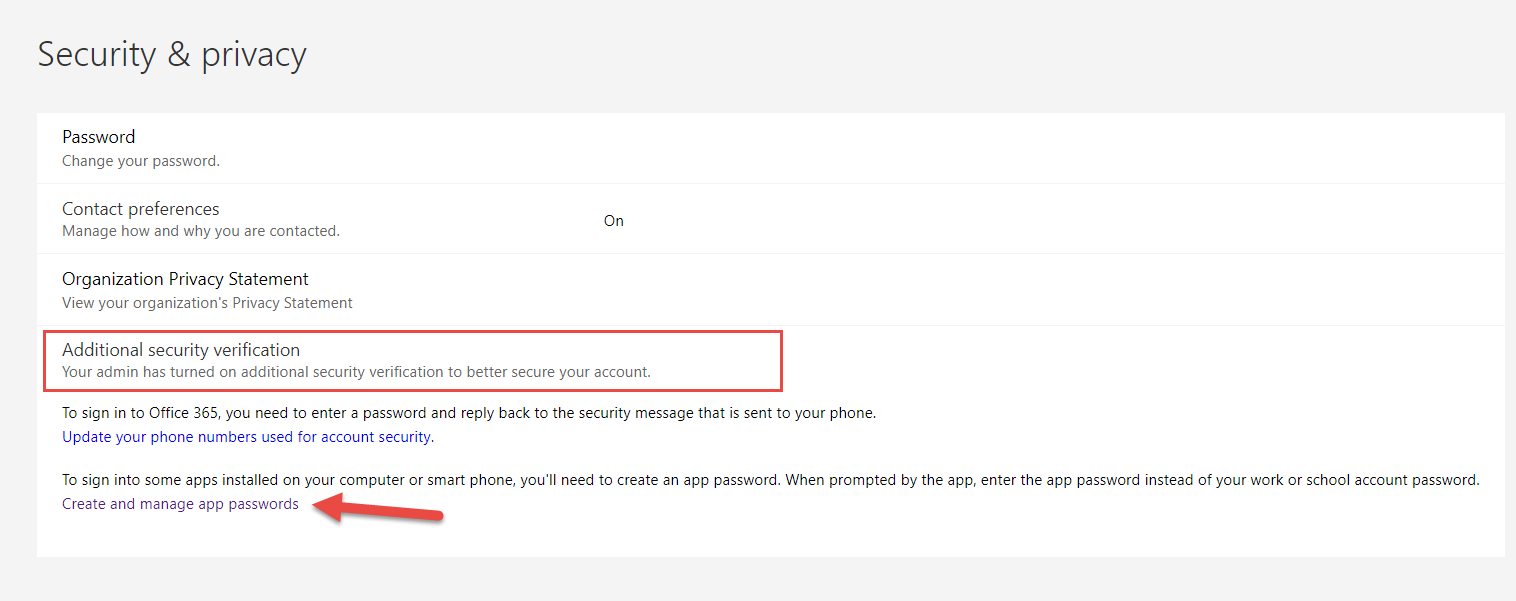
Select Additional Security Verification. To configure an app password. Enter any name and click on the next button.
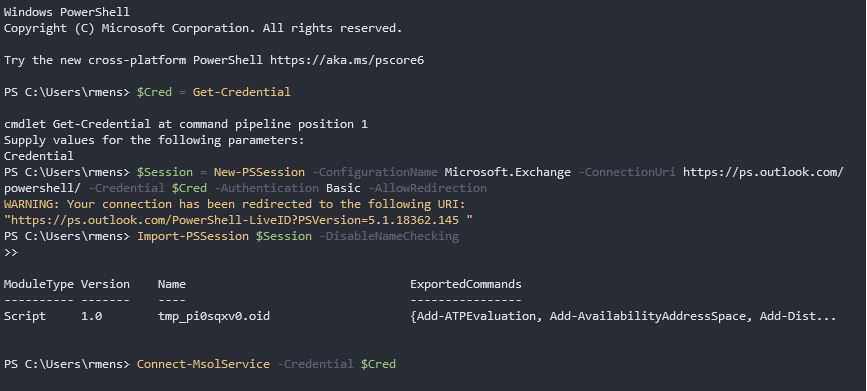
Use these commands to specify a password for a user account. Powershell would be easier for obvious reasons. Here is the syntax for the New-MSOlUser cmdlet.
Sign in to your Office 365 admin center. 3 Run the credentials script to create the username and password encrypted text files. The Admin Centres for Office 365 and for Exchange Online are great for simple and singular tasks regarding password management and policy however if you wish to carry wider tasks or bulk user management PowerShell is the best option.
The only way is via the portal. Try using below code to avoid pop-up asking for App Password. Which app in particular do you need them for afaik all first-party ones support Modern auth now.
UserUPN newPassword Set-MsolUserPassword -UserPrincipalName userUPN -NewPasswordMissing. You can refer to this document at the allow users to create app password section. Click Create and manage app password.
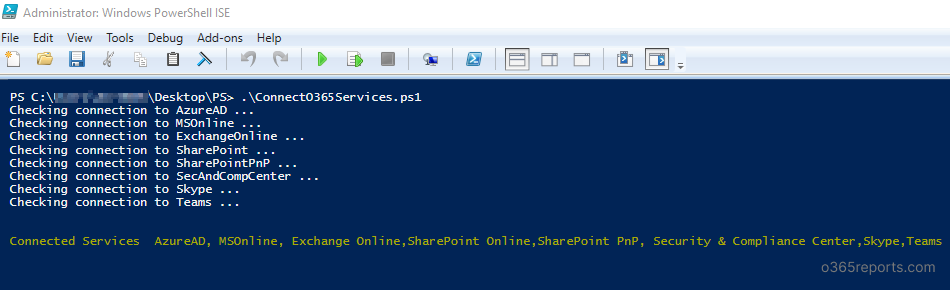
First connect to your Microsoft 365 tenant. Kernel Office 365 Migration Software Video Tutorial. Navigate to httpsakamsmfasetup and select the App Passwords menu.
Only Enforced Users can create app passwords Allow users to create App Passwords in Office 365 Multi-factor Authentication Now lets select Priyeshs user settings by selecting the user and then going to Manage User Settings. I realize I can do this in the Azure portal but only with the GUI. Starting from the recently released version 3 Veeam Backup for Microsoft Office 365 allows for retrieving your cloud data in a more secure way by leveraging modern authentication.
Powershell to Generate App Passwords. You can refer to this document at the allow users to create app password section. PowerShell is a cross-platform Windows Linux and macOS automation tool and configuration framework optimized for dealing with structured data eg.
In case that you need to export Active Directory on-Premise user account based on a specific parameter you can use the PowerShell cmdlets named get-aduser you will need to use PowerShell console from DC or import the Active Directory cmdlets to the existing PowerShell console. Create App Passwords from My Sign-ins page As shown in the beginning try to Add a new method This time youll be able to see App Passwords as an option to select. Wait for couple of minutes for Office 365 propagation and then use the app password.
And you should really be avoiding the use of app passwords they are an crappy workaround which needs to die. 2 Create an App Password for the user account. Location securecred Get-Credential securecredUserName ConvertTo-SecureString -AsPlainText -Force ConvertFrom-SecureString set-content.
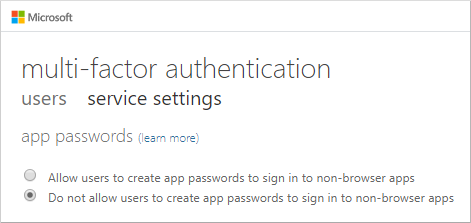
After clicking Next the window will display the app password and you should save it in a password credential manager as you wont be able to retrieve it. On the multi-factor authentication page select the Allow users to create app passwords to sign in to non-browser apps option. Selet Named location from the left navigation blade.
To log into Office 365 in PowerShell you need the UPN of an Office 365 Global Admin and the password. Provisioning Office 365 user and export information from Active Directory. Id like to see which users have created app passwords and remove them for selected users all with Powershell.
Login to the Microsoft 365 Admin Center. 1 MFA is enabled on the Office 365 user account. In the bolded line below you can see the out-file command is expecting to send this to a folder structure of CO365Key.
Search for and select Azure Active Directory then choose Users. There are not quite as many options but the process is very similar. Powershell to Generate App Passwords.
You can choose to copy password to clipboard Now go to the Kernel application and use the app password to login to your Office account. Open the User account by clicking on your profile image or initials in the top-right corner of the screen and selecting My account. Open the Security and Privacy tab Figure 4.
My Application need more premissions from service principals such as Office 365 Management APIs and Skype and Teams Tenant Admin API. Select it and click on Add Next you can give a name to the App Password you are setting. In this first step we will create the encrypted password key which we will use in our login script.
In that way I cant create the app because the ResourceAppId isnt correct. This is a strong password that you can use for an app that doesnt support MFA. To create a user in Office 365 by using the Azure AD module I use the New-MSOlUser cmdlet.
To create an app password. PowerShell includes a command-line shell object-oriented scripting language and a set of tools for executing scriptscmdlets and managing. Select Create and manage app passwords last line Create a new App Password for PowerShell.
Click on Configure MFA trusted IPs in the bar across the top of the Conditional Access Named Locations window. Admin could enable user to create app password but heshe cannot create app password for them. In manage Settings for this user youll see the option Delete all existing app passwords generated by the selected user.
But when I get all service principals in a variable it seems that I cant assign all the AppIDs to the ResourceAppId properly. For backup and restores you can now use service accounts enabled for multi-factor authentication MFA. Now an app password is created successfully.
You can give it a suitable name keeping in. You can now create an app password for a User. JSON CSV XML etc REST APIs and object models.

Ramesh Natarajan Google Active Directory Windows Server 2012 Windows Server

Office 365 App Password And Multi Factor Authentication

Skype Room System Provisioning Steps For O365 Business Server System Office 365

How Can You Reset Or Change Your Password In Microsoft Office 365

Using Office 365 Powershell With Mfa Enabled Youtube
Creating An App Password For A Azure Ad Account Using The Office 365 Portal Johanpersson Nu
Connect To All Office 365 Services Powershell Supports Mfa Too
Configure App Passwords For Azure Ad Multi Factor Authentication Azure Active Directory Microsoft Docs

Configure Office 365 Atp Like A Pro With Orca Daniel Chronlund Cloud Tech Blog

Access Office 365 Authentication Popup Of Powershell From Windows Form Wpf Stack Overflow
Sign A User Out Of All Office 365 Apps And Sessions

Pin By Patrick Guimonet On Microsoft 365 Behavioral Model Sharepoint Smb

Manage Office 365 Users Passwords Using Powershell Office 365 O365info Com

Reducing It Complexity Surface Autopilot M365 Sharepoint Surface Complex

Setting Up Office 365 Password Policy Notifications Guide Syskit

Deploying A Kiosk Using Windows Autopilot Deployment Sharepoint Kiosk App

Office 365 App Password And Multi Factor Authentication

All In One Powershell Script To Perform Office 365 License Management And Reporting In A Jiffy R Office365
